Fake Base Station problem in 5G
Continuing with the previous blogpost, we discuss the problem of fake base stations in general and a number of protection measures added in 5G standards.
IMSI catcher is a device to identify and track cellular phone subscribers. This is achieved by locating the presence of permanent cellular identities such as International Mobile Subscriber Identity (IMSI) tied to the subscriber’s (U)SIM card, and International Mobile Equipment Identity (IMEI) tied to the mobile device. Due to network design architecture vulnerabilities [1, 2, 3, 4], IMSI catcher types of attack are possible in 2G, 3G and 4G networks. There are plenty of reasons why those architecture vulnerabilities are not fixed in 4G networks – reasons revolve around tradeoff between network performance/availability and privacy.
Finally, after 20 years cellular networks in 5G generation have added several protection methods to address fake base station problems. The 3GPP 5G security standard document presents these new methods and we highlight a few of them here:
- The home operator, for example, your (U)SIM card provider is able to conceal the Subscriber Permanent Identifier (SUPI). This will be achieved using Elliptic Curve Integrated Encryption Scheme (ECIES)-based protection scheme with the public key of the Home Network stored in 5G (U)SIM and concealed identify is named as Subscription Concealed Identifier (SUCI).
- The mobile phone-supported network-based fake base station detection framework is proposed. The goal of this framework is to assist mobile phones to detect fake base stations by using legitimate information from the serving network.
The above features indicate that fake base stations in 5G will not receive SUPI (which is equivalent to IMSI in 2G, 3G, 4G) after camping on them. However, if the 5G phone is downgraded to 4G or 3G networks then fake base stations can steal IMSI of the mobile subscriber. Interestingly, SUPI protection environment will be available in 5G StandAlone (SA) mode type of networks only. Hence, probably more than 95% of 5G Non-StandAlone (NSA) deployments can be affected to fake base station-based privacy issues.
Also, a new framework to detect a fake base station is proposed in [33.501]. Detecting such types of fake base stations is a challenging problem too.
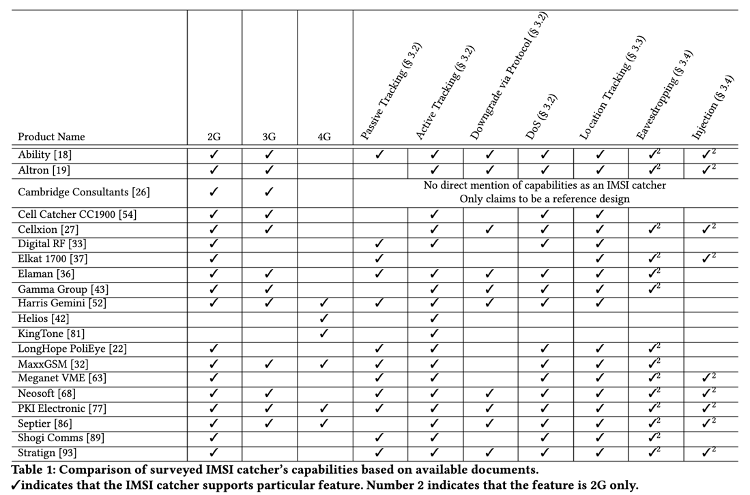
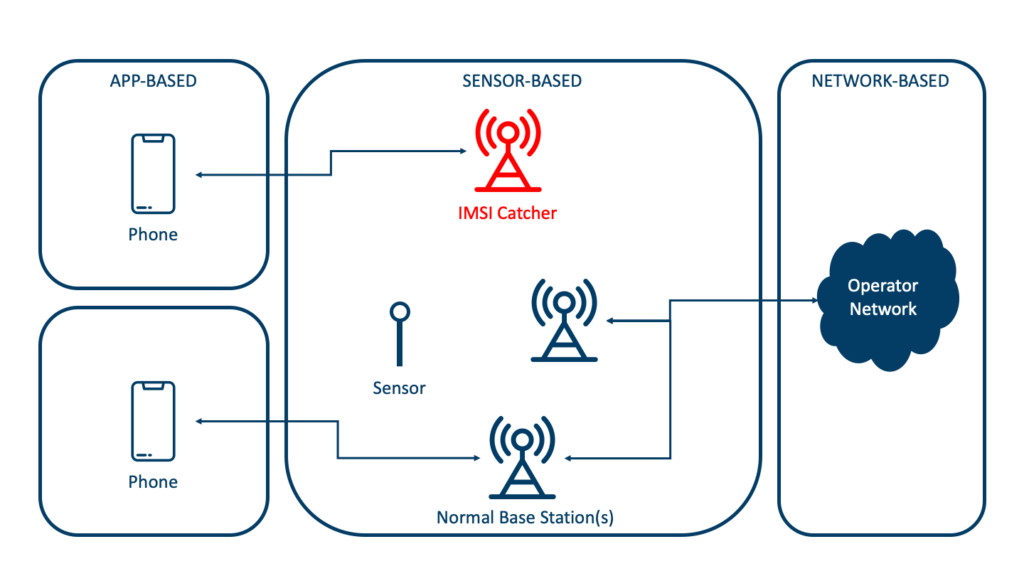
Recently, our researcher, Dr. Ravishankar Borgaonkar, did a study together with researchers from TU Berlin to understand the anatomy of IMSI catcher problem and detection methodology. In this paper1, we did a systematic study of IMSI catchers, especially commercially available ones. Starting from publicly available product brochures, we analyzed information from the international patent databases, attacking techniques used by them and vulnerabilities exploited in cellular networks (2G, 3G, and 4G). Based on the collected data sets (as shown in Figure 1), we perform a survey of IMSI catcher detection techniques and their limitations (Figure 2 shows types of detection methods). Note that in the past, we did investigate and evaluated IMSI catcher detection applications, including Android applications, a full paper can be found here2. To conclude, we provided insights that we believe help guide the development of more effective and efficient IMSI catcher detection techniques.
To conclude, until we move towards 5G SA networks and the mobile phones will able to lock their phones for 5G SA network ONLY, the proposed IMSI catcher protection measures will not be effective, and more research efforts are needed to tackle privacy problems in future cellular networks beyond 5G.
Hacking 5G Network supporting the future 5G Hospital

Ultrahack organized the very first 5G security hackaton in Oulu, Finland from the 29th November to the 1st December 2019. Hackers from all around the world gathered for a two-day event around 5G security. From SINTEF, Guillaume Bour participated to this hackaton along with team of security researchers from Finland, France and Germany.
Three challenges were available during this hackaton for hackers to play with. In particular, the “Future 5G Hospital Intrusion Challenge” which we took part in.
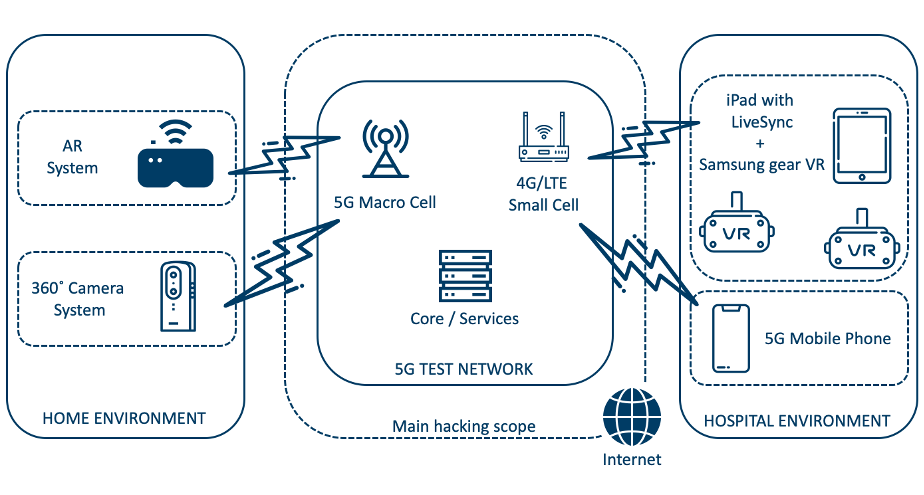
A Nokia 5G Test network deployed on the Oulu University campus was used to host the challenge. Several scenario were reproduced, using different technologies such as Augmented Reality (AR) glasses and a 360 video camera to replicate the visit of a nurse to a patient’s home; or 5G Virtual Reality (VR) glasses and 5G phone to replicate the hospital environment where a doctor can see what the nurse sees and advise on the best actions to take for the patient.
In practice, the environment was built with a 5G network operating in a Non-StandAlone network architecture. The different devices were connected to either the 5G-NR station linked to an 4G/LTE EPC (the AR glasses for instance) or to an 4G/LTE cell. The goal of this track was to disrupt the critical functionalities of the future hospital. The teams were provided with USIM cards that could connect to both the gNB and the eNB.
Learnings from this experience can be found on the medium we wrote together with the team.
Take-aways for securing 5G networks
Based on our research [1, 2, 3, 4] and considering our experience in hacking a live 5G hospital network, we conclude that securing multigenerational 5G network is a challenging task, requiring to deploy mandatory 3GPP standard features and effectively follow best practices in securing IT/cloud systems.
Finally, a few take-aways from our hackathon experience are:
- A missing network segmentation and isolation, allowing potential attackers to scan other network range that they are not supposed to have access to.
- Exposure of critical services, like a management interface.
- Regular security vulnerabilities like weak SSH passphrase, default credentials or lack of hardening on the server, helping potential attackers to escalate their privileges and earn their way forward into the system.
More information about the above points can be found in our post on medium, where we replicated such a scenario and tested it against several attack hypotheses.
- [CCS2019] – Shinjo Park, Altaf Shaik, Ravishankar Borgaonkar, and Jean-Pierre Seifert. 2019. Anatomy of Commercial IMSI Catchers and Detectors. In Proceedings of the 18th ACM Workshop on Privacy in the Electronic Society (WPES’19). Association for Computing Machinery, New York, NY, USA, 74–86. DOI:https://doi.org/10.1145/3338498.3358649
- [USENIX2017] – Ravishankar Borgaonkar, Andrew Martin, Shinjo Park, Altaf Shaik, and Jean-Pierre Seifert. 2017. White-stingray: evaluating IMSI catchers detection applications. In Proceedings of the 11th USENIX Conference on Offensive Technologies (WOOT’17). USENIX Association, USA, 21.
