The world is fighting against a fairly unknown enemy named COVID-19 and preparing in every possible way to win the battle. One of the strategies to reduce the spreading of COVID-19 virus is “contact tracing”. This “contact tracing” means to find out potential people who may have been exposed to this virus. The manual and resource-constrain tracing procedure are usually started once the doctor confirms the positive patient and health official will start interviewing him/her about possible contacts in the last few days. Eventually, the collected data will be dependent on the recall and memory of interviewees. To automate this manual procedure and assisting health officials effectively, a few countries have started the use of digital solutions. Such digital solutions currently use different mobile phone technologies to trace contacts, thanks to the wide-reach of smartphones to almost most of the county/world population.
The mobile technologies for contact tracing include two types mostly –
1. A dedicated mobile app
In this category, citizens are asked to download the app (voluntarily or mandatory depending on the government regulation). The primary idea is assisting health officials to inform App users who are close contacts of the virus as soon as possible. The secondary benefits of such an App could be as follows:
- Record suspected COVID-19 symptoms (as done by FHI in Norway)
- Provide an authenticated certificate of COVID-19 test (this may be used in some cases, for example, in future where required for travel to certain country or place)
- Provide electronic passes for a certain category of workers in case of national/emergency lock-down
From the technology perspective, these apps will be utilizing GPS and low-power Bluetooth based proximity location features available in today’s smartphones. Further, apps need to collect data of nearby mobile devices and send them to the server continuously for the processing. This process, however, introduces security/privacy challenges for the governments and citizens as well.
*Security and Privacy Challenges & Vulnerabilities *
The main security challenges are following best software security practices while RAPIDLY designing/developing the system design, smartphone apps, and cloud-based servers/APIs for storing/processing the citizen’s data. In addition, security analysis of app source code if released as open-source or closed-source and pen-testing of APK at least to avoid leaking of sensitive keys/configuration data, etc.
More importantly, it is very challenging to de-anonymize, de-centralized, and encrypt the smartphone collected data so that privacy and anonymity of the App owners will be preserved by following national/EU regulations. Also, battery performance and usability aspects are also important from app users perspective.
Recently, Apple and Google joined the effort to enable the use of Bluetooth technology for contact tracing apps, with user privacy and security central to the design. However, their approach is to enable OS layer support for developing contact tracing apps instead of the application layer. There is a detailed analysis of this Google Apple Contact Tracing (GACT) approach, suggesting potential issues.
A list of country-wise released official apps can be found here . It also contains apps that released their technical details and source-code. There are also university-wide and EU level initiatives such as PEPP-PT, DP3T, and MIT – with a focus on data security and privacy aspects. However, a recent study reveals severe risks to society from the PEPP-PT approach. In particular, private encounters of reported people may be revealed, and people may be coerced to reveal the private data they collect.
A data breach is reported in the contact tracing app developed in Belgium. The user names, email addresses, and encrypted passwords were exposed to the attacker.
Considering privacy issues, the European Data Protection Board published a letter on the European Commission’s draft Guidance on contact tracing apps. The letter suggests ” the development of the apps should be made in an accountable way, documenting with a data protection impact assessment all the implemented privacy by design and privacy by default mechanisms, and the source code should be made publicly available for the widest possible scrutiny by the scientific community.“
In addition to the EU, an academic and scientific community across the word released an open letter with a message – contact tracking app or technology should be decentralized, transparent, voluntary, & should not be usable for purposes beyond the COVID-19 response.
2. Mobile (2G/3G/4G/5G) network data-based approach
In this approach, the data stored at the mobile network operator side can be used for tracing COVID-19. This data is usually stored during normal phone operations such as when making a phone call or receiving SMS or surfing the Internet using 2G/3G/4G/5G networks. In technical terms, our mobile phones in ideal or operational mode, report their location (using triangulation methods via base station identities) to the network providers.
The centrally stored data can be used for providing the approximate location of a mobile phone. In addition, the same information can be used to draw a map of previously visited locations or a travel-path of a particular mobile user.
Discussion around ‘how to get access to such mobile data sets or who should get access legally’ can be debatable at this stage. However, there is a possibility to hack into these data sets due to SS7 vulnerabilities in the mobile network architecture.
Some countries have started to use these mobile network data sets for tracing and tracking purposes too. In India, a state is using base station location data for COVID-19 tracking and alerting system. For example, the following figures 1 and 2 shows software used by the Israeli government.
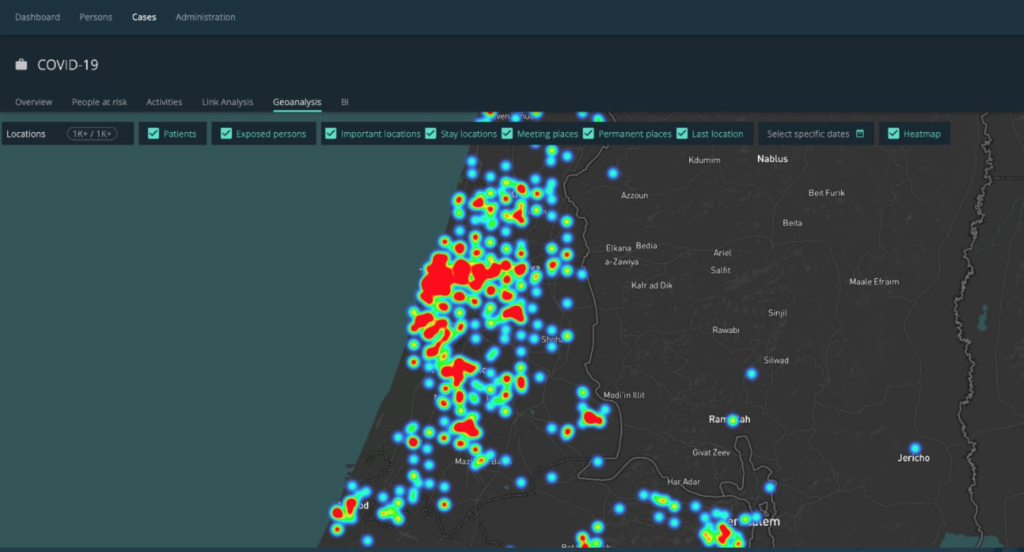
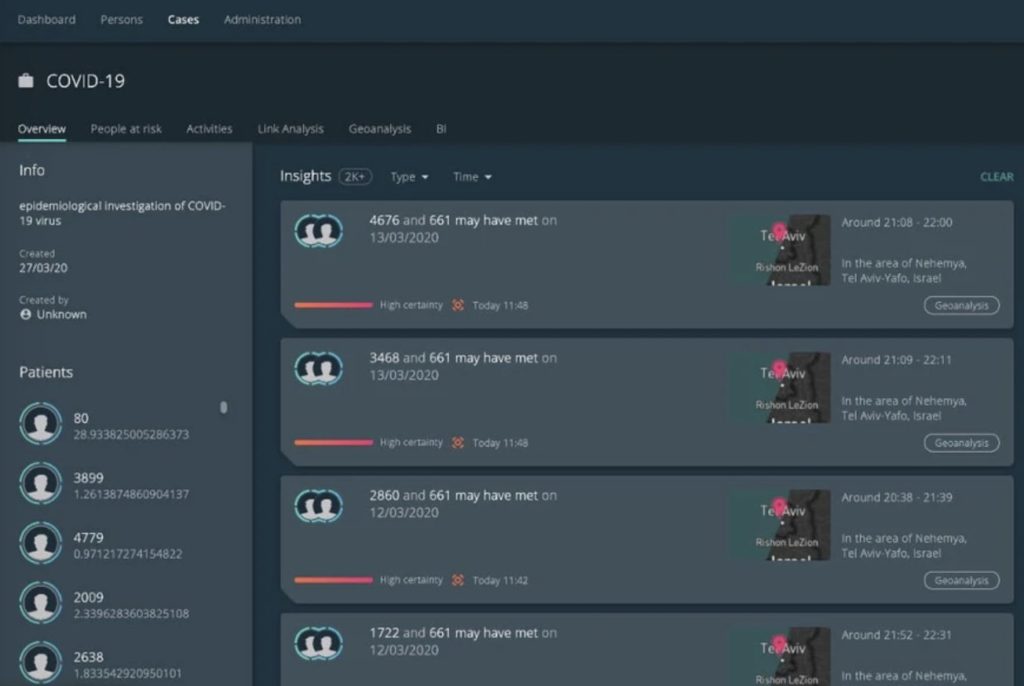
Interestingly, Telenor in Norway using mobile network data sets for predicting and preventing the spared of the virus. This is a different approach than tracing a particular COVID-19 case.
Challenges with the mobile data based approach:
- No option to opt-out for mobile users
- Legal aspects of using surveillance technology on citizens
- Anonymity and privacy of the data collected from mobile network operators
*Innovative ideas from mobile network technologies for the awareness*
There are other features of mobile networks useful for increasing awareness about the disease and providing alerts/messages. A few examples are as follows:
- SMS messages for providing health emergencies (yes, fake SMS is an issue for creating panic or frauds)
- Ringing tones informing best hygiene practices/ precautions in public
- Informing “StayHome” information via radio protocols (see example here )
In conclusion, we already sitting on big mobile-data sets that know our travel paths, habits, lifestyle, etc and hinting to go toward designing and building a privacy-preserving post-5G era after the arrival of the smartphone era in every corner of the world. But, priority should always be to use all possible technologies to protect and help our society.
